 Aircrack-ng is a whole suite of tools for Wireless Security Auditing. It can be used to monitor, test, crack or attack Wireless Security Protocols like WEP, WPA, WPA2. Aircrack-ng is command line based and is available for Windows and Mac OS and other Unix based Operating systems. Aircrack-ng suite contains a lot of tools used for various purposes but here we’ll only look at some important tools that are used more often in Wireless Security testing.
Aircrack-ng is a whole suite of tools for Wireless Security Auditing. It can be used to monitor, test, crack or attack Wireless Security Protocols like WEP, WPA, WPA2. Aircrack-ng is command line based and is available for Windows and Mac OS and other Unix based Operating systems. Aircrack-ng suite contains a lot of tools used for various purposes but here we’ll only look at some important tools that are used more often in Wireless Security testing.Airmon-ng
The BSSID (mac address) of the router; The Channel of the router; A wireless router broadcasts the WiFi signal on channels ranging from 1 to 11. In this case, our router is on channel 1. The BSSID (also called a mac (media access control) address) is an address which specifies the router’s network card. Aircrack-ng: Download and Install. The Latest Version Only: If you really want to hack WiFi – do not. Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. The application works by implementing the standard FMS attack along with some optimizations such as KoreK attacks, as well as the PTW attack. As far as I know, you can't use airmon-ng on MacOs, they're for Linux only. The best way I can suggest for you is using sudo airport -s to determine which SSID and its channel you want to attack, after that, sudo airport en0 sniff x to capture packages of all SSIDs which located at channel x, en0 or en1 is the wifi setting of your mac, you can go to 'About this mac - System Report - Network. Make sure you have Xcode installed on your Mac, which can be found on the installer CD/DVD which came with your Mac. After getting the source you can do a simple “make && sudo make install” from the untarred directory. When you use the stable, you need to rename the Makefile.osx to Makefile and when you use the dev version it will.
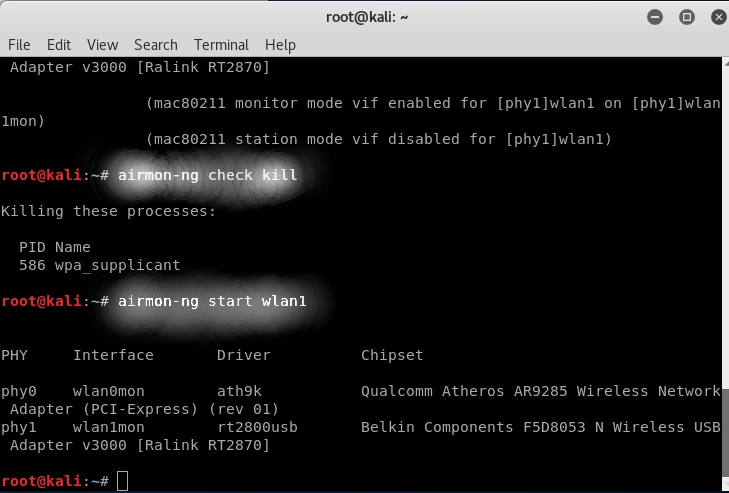
Airmon-ng is used to manage wireless card modes and to kill unnecessary processes while using aircrack-ng. To sniff a wireless connection, you need to change your wireless card from managed mode to monitor mode and airmon-ng is used for that purpose.
For instructions, see Install an older version of Adobe Reader on Mac OS. Double-click the.dmg file. (If you don't see the Safari Downloads window, click Finder (User Name) Downloads.). 
Airodump-ng
Airodump-ng is a wireless sniffer that can capture wireless data from one or more wireless Access Points. It is used to analyze nearby Access Points and to capture handshakes.
Aireplay-ng
Aireplay-ng is used for replay attacks and as packet injector. It can be de-authenticate users from their APs to capture handshakes.
Airdecap-ng
Airdecap-ng is used to decrypt encrypted WEP, WPA/WPA2 wireless packets with known key.
Line 6 driver for mac. Aircrack-ng
Aircrack-ng is used to attack WPA/WEP wireless protocols in order to find the key.
Aircrack-ng is easy to install in Ubuntu using APT. Just type the following command and this will install all tools available in Aircrack-ng suite.
sudoapt-get install-y aircrack-ng
Usage
In this article, we’ll take a quick look at how to use aircrack-ng to crack an encrypted wireless network (TR1CKST3R in this example) to find the password.
First of all, list out all available wireless cards connected to your PC using ‘iwconfig’ command.

We’ll use ‘wlxc83a35cb4546’ named wireless card for this tutorial (This might be different in your case). Now, kill all the processes running on wireless card using airmon-ng.
Start Monitor mode on ‘wlxc83a35cb4546’ by typing
ubuntu@ubuntu:~$ sudo airmon-ng start wlxc83a35cb4546
Now, airmon-ng has started Monitor mode on wireless card, it’ll appear as different name ‘wlan0mon’. Run ‘iwconfig’ again to list wireless details.
Then, use airodump-ng to see nearby Wireless Access Points and their properties.
You can narrow down search using MAC (–bssid) and channel (-c) filters. To capture handshake (Handshake contains encrypted password), we need to save our packets somewhere using “–write” option. Type,
-c11 wlan0mon --write/tmp/handshake.cap
--bssid : Access Point’s MAC Address
-c : Access Point’s channel [1-13]
--write : Stores captured packets at a defined location
Now, we need to de-authenticate every device from this Access Point using Aireplay-ng utility. Write
-a : Specify Access Points MAC for Aireplay-ng
-0 : Specify number of deauth packets to send
After a while, all devices will be disconnected from that Access Point, when they’ll try to reconnect, running airodump-ng will capture the handshake. It’ll appear at the top of running airodump-ng.
Airmon Mac Os X
Handshake is stored in ‘/tmp/’ directory, and contains encrypted password that can be brute forced offline using a dictionary. To crack the password, we’ll be using Aircrack-ng. Type
/usr/share/wordlists/rockyou.txt
-w : Specify the dictionary location
Aircrack-ng will go through the list of passwords, and if found, it’ll display the password used as key.
In this case, aircrack-ng found the password used ‘123456789’.
Now, stop Monitor mode on wireless card and restart the network-manager.
Airmon For Macbook
ubuntu@ubuntu:~$ sudo service network-manager restart
Airmon For Mac Os
Conclusion

Airmon For Macbook Pro
Aircrack-ng can be used to audit Wireless Security or to crack forgotten passwords. There are some other similar tools available for this purpose like Kismet but aircrack-ng is better known for good support, versatility and having wide range of tools. It has easy to use Command line interface which can easily be automated using any scripting language like Python.
